For almost two years, I dealt with a situation where I had access to a gigabit ethernet connection to the Internet, but I couldn't harness it since I was behind a commercial firewall that only supported 100 Mbps. Upgrading would have required thousands of dollars which, especially in this economy, seemed wasteful. My solution was to create a Linux-based gigabit ethernet firewall that'll do the same thing. The beauty of this setup was not only that I could put together the hardware for less than $1000, but since the software is freely copiable, there are no restrictions on the numbers of users and licenses.
It's clear that gigabit ethernet over copper is going to be the next step in networking. Even if you don't have a gigabit ethernet connection to the Internet, it's not too expensive to acquire one. It's also clear that one of the most logical ways to protect yourself from unwanted attack is through the use of a firewall. However, commercial firewall products utilising gigabit ethernet are prohibitively expensive.
The machine I purchased for a firewall is a nice 4U rackmount with an AMD Palamino 1700+ CPU, a MSI KT3 Ultra2 KT333 MS-6380E motherboard, a small hard disk, some memory, and three Intel Pro/1000T Gigabit Server ethernet cards. All the hardware cost less than $1000. The main thing here is to note any computer with the gigabit ethernet cards should do, assuming that its components work well with Linux (which in most cases, they should).
The operating system running on the firewall is Linux, and we use the KRUD distribution, version 8.0 (http://tummy.com/krud). The system is installed like any other Linux system, but all Internet-based services are turned off.
Linux supports firewalling through its netfilter/iptables subsystem (http://www.netfilter.org). It will basically let you do anything a commercial firewall can do, and then some, including the functionality of packet filtering (stateless or stateful), all different kinds of NAT (Network Address Translation) and packet mangling. It is extremely powerful, but cumbersome to use.
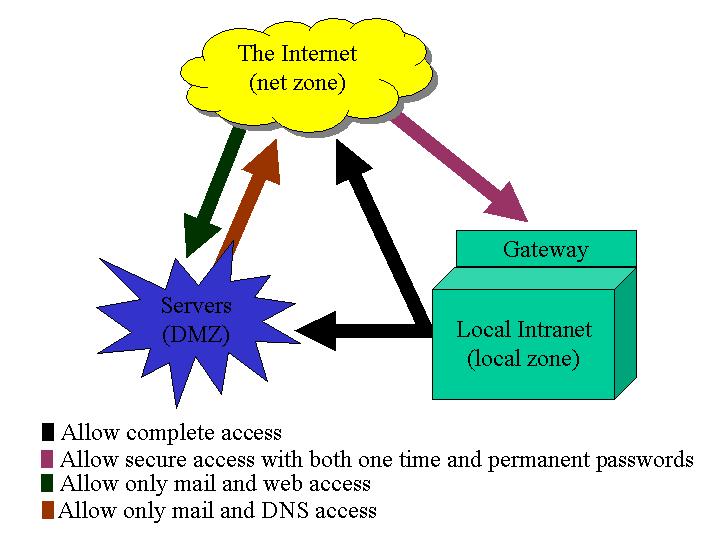
There are packages that provide a cleaner interface to the iptables: One such package that we use is shorewall (http://www.shorewall.net), which lets you manipulate the firewall rules using simple configuration files. Our setup is such that each of the gigabit ethernet cards is assigned to three zones: the zone that compromises the external Internet ("net"), the demilitarised zone ("dmz"), and the local network ("loc"). Using shorewall, we can specify how traffic is to be routed across the different zones.

Specifically, we allow all connections from machines in the local zone to the net zone. We allow web and mail access to our web/mail server(s) located in the demilitarised zone (DMZ); for this reason, all machines in the DMZ are completely mirrored since web and mail servers, even the most up-to-date versions, could have potential security holes. Depending on your level of paranoia, you can set up the firewall such that you allow access to the firewall only from a console, or from a single host in the local zone.
We allow only secure logins, using openssh (http://www.openssh.com), from a selected list of trusted hosts in the net zone to a dedicated gateway machine (located in the local zone). The secure logins have to pass a one-time password screen based on opie (http://www.inner.net/opie), as well as a permanent password screen, to be able to log into the gateway machine. The combination of openssh and opie for authentication is handled using Linux PAM (http://www.kernel.org/pub/linux/libs/pam/).
The two-password system is to address the issue of keyloggers who may record a user's permanent password (which is possible even over a secure connection). One-time passwords get around this problem, but they are not enough since users have a tendency to store their list of one-time passwords on their computers, and a computer could be stolen/compromised.
Thus the only way to gain access to our local network from the Internet is by knowing the list of one-time passwords, and the permanent password for an authorised user, and make the connection from a list of trusted hosts. The passphrase for the one-time passwords is randomly generated for each user (i.e., the users don't have a choice as to the passphrase), which is then used to generate a list of one-time passwords that a user keeps. The list can be reset at the whim of the user, with a new random passphrase being used to create a new list. A script to do this is available (http://www.ram.org/computing/linux/firewall/otpgen.tgz).
The downside of such a firewall is that you do need to know your Linux, and be extremely familiar with networking principles. Even though the shorewall packages simplifies the management, for optimal security, it helps to be familiar with the netfilter subsystem. If your system administrator is familiar with Linux, then this should not be a problem.
The amount of flexibility greatly outweighs the shorewall learning curve. Not to mention the cost of creation and maintenance. Another singular advantage to a commercial product is that it's easy to upgrade the hardware and software at whim.
The bottom line is that security is best achieved by a thorough understanding of networking principles and exploits. A Linux-based firewall gives you the freedom, flexibility, and the opportunity to achieve secure in an optimal and economical manner.